Unlocking the Secrets of Smart Lock Security: A Chat with Tedee’s Grzegorz Chuchra
Today, we’re diving into the dynamic world of smart lock security with Grzegorz Chuchra. As the Co-founder & CEO of Tedee and former CEO of Predica, Grzegorz brings a wealth of experience and leadership to the table.
With a Master of Engineering in Computer Software Engineering from Warsaw University of Technology, complemented by a prestigious one-year scholarship at London South Bank University, and an MBA from Warsaw University of Technology Business School in collaboration with renowned institutions like London Business School, HEC, and NHH, Grzegorz is a seasoned expert in both technology and business strategy.
Join us as we delve into the fascinating realm of smart lock security and explore the future of home access control. Let’s get started!
To start off, could you explain what exactly a cloud is in the context of smart door locks, and how it operates within the system?
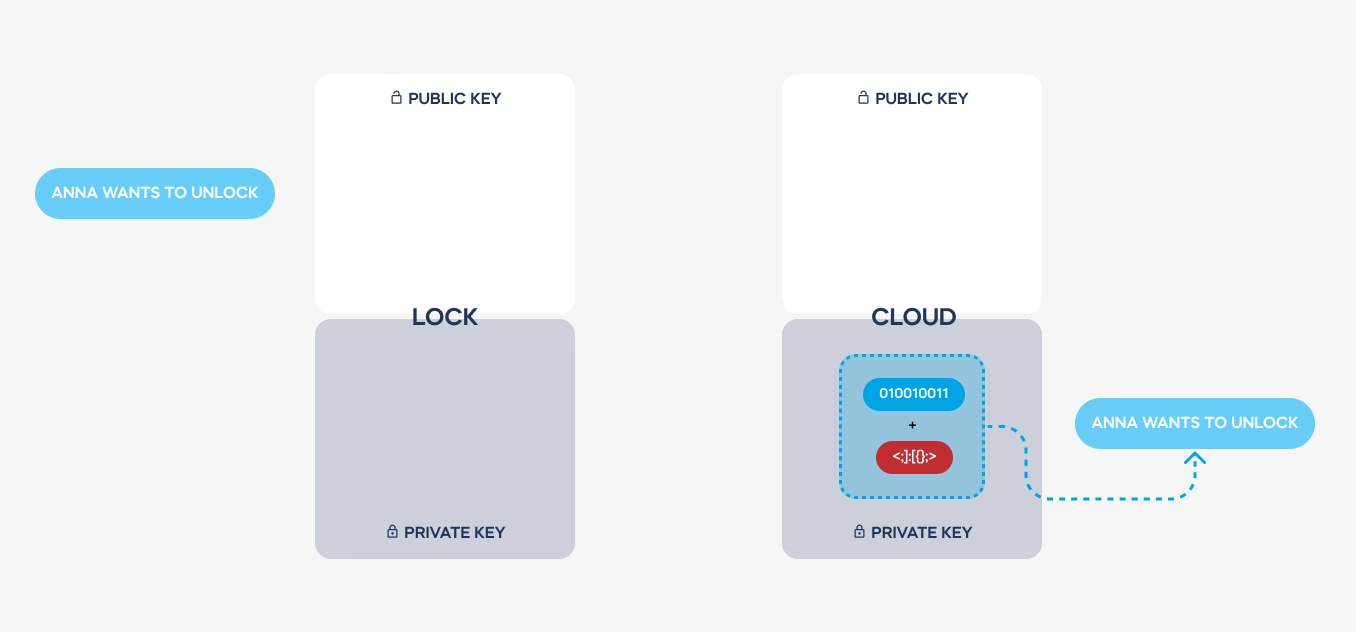
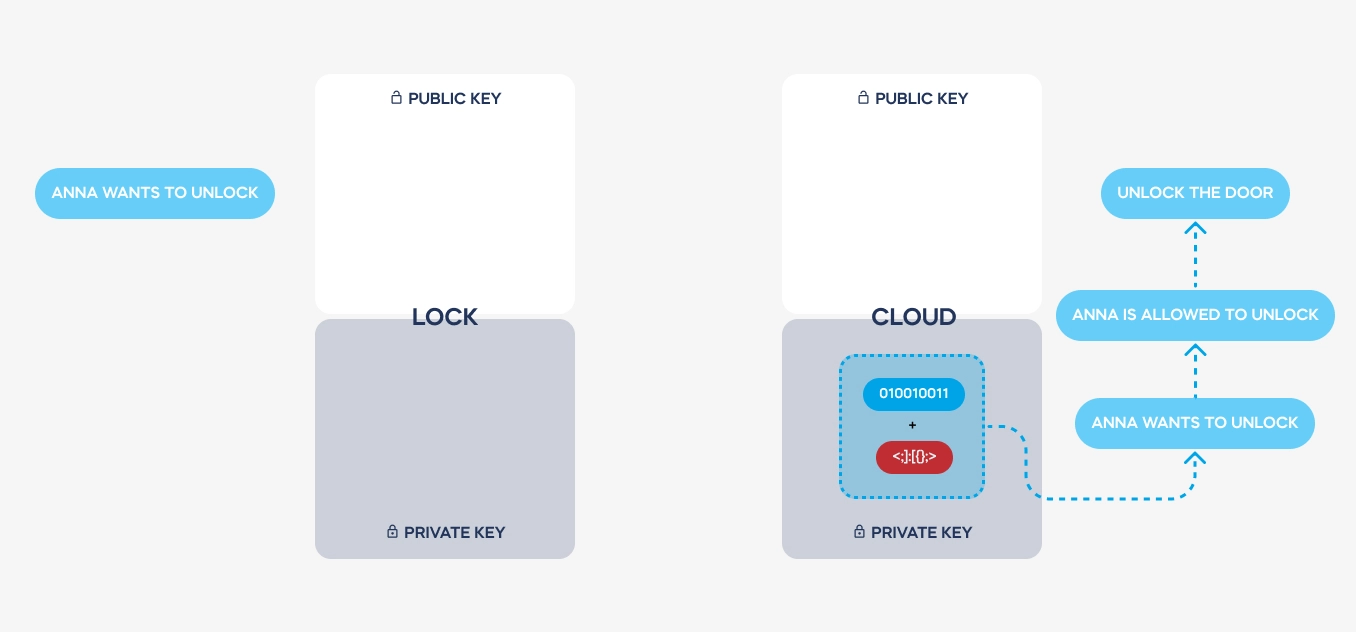
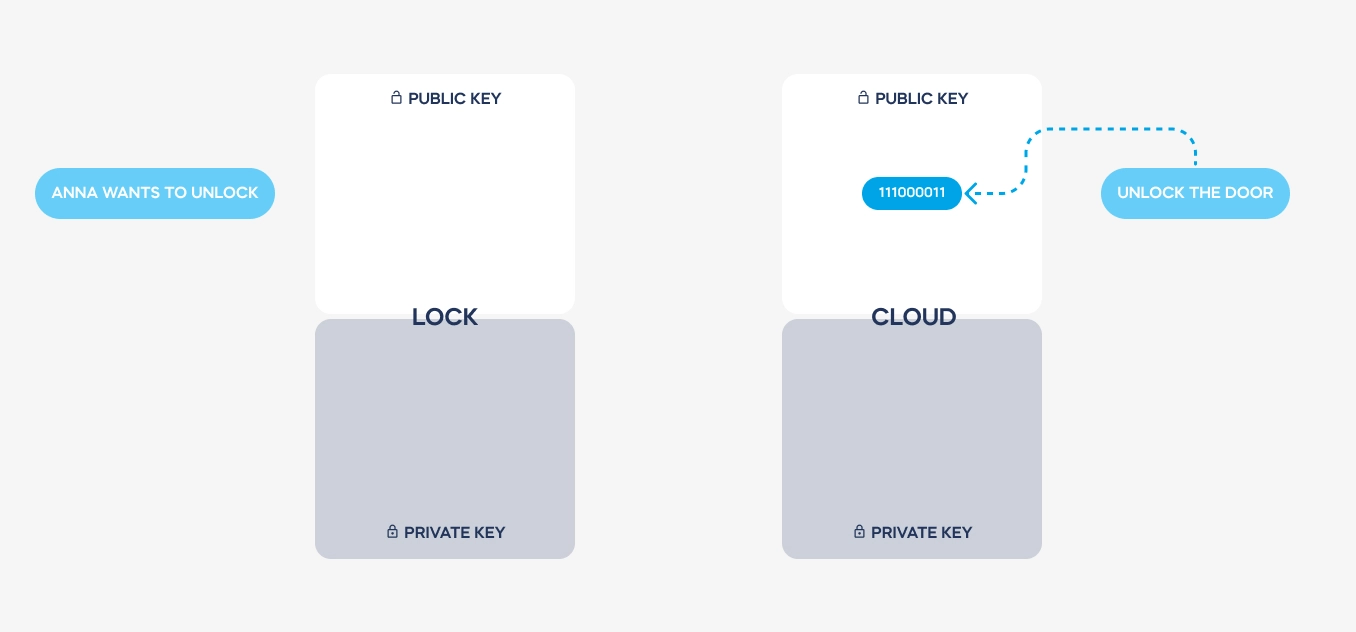
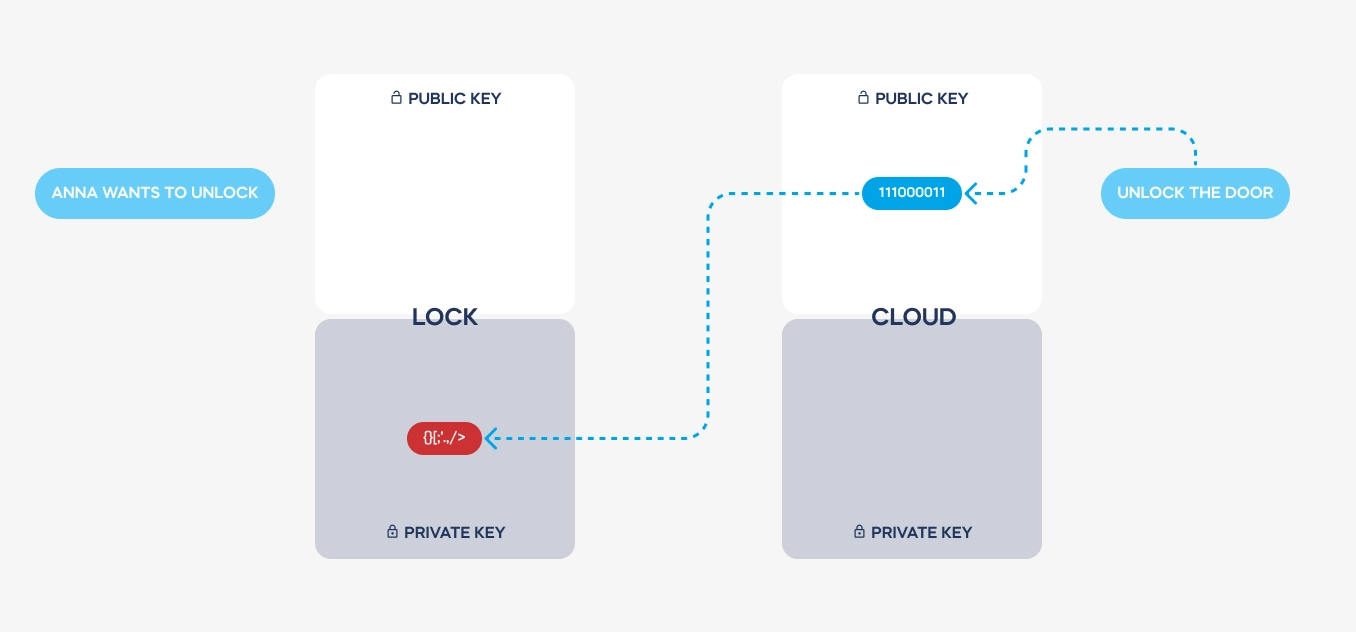
Grzegorz Chuchra: Certainly. When we talk about the cloud in relation to smart door locks, we’re referring to an online server-based security system. Think of it like online banking, where complex security measures authenticate your identity and permissions. This cloud-based system sends validated signals to your lock, allowing it to unlock if approved. It essentially acts as the backbone of the security infrastructure, enabling advanced technology and integration with various smart home systems.
So, why should someone opt to unlock their door through a cloud-based system?
GC: That’s a great question. If we want to control a lock remotely beyond the range of BLE (like how headphones connect to phones – max. 10m), there’s no other option. We have to use a cloud-based service. Whether it’s hosted by a company like Tedee or by Hyper-Scalers (Amazon, Microsoft, or Google). From my experience, I know that the safest, most reliable option is one of these. That’s why both banks and public institutions (even the Pentagon – as far as I know) use the cloud.
There’s often concern about the security of cloud-based systems. How would you address these concerns, especially in the context of smart locks?
GC: It’s understandable that people may have reservations about entrusting their security to the cloud. However, it’s important to recognize that the cloud environment is rigorously secured, often exceeding the capabilities of individual users or organizations. Banks, for example, rely heavily on cloud-based systems for their operations, which speaks to the level of trust placed in these platforms. By leveraging the expertise of cloud vendors and undergoing thorough security testing, we can ensure that smart locks remain resilient against potential threats.

Moving on to the topic of hacking, can smart locks be hacked? And if so, what measures are in place to prevent this?
GC: Yes, the smart lock like digital system can be hacked. But Tedee’s security architecture is designed and implemented in the way that make it equally hard to hack like your banking app. Wireless communication forms the backbone of smart lock systems, connecting smartphones, locks, and the cloud. However, these connections are far from simple; they operate on sophisticated protocols designed to prevent unauthorized access. For instance, Tedee utilizes the latest TLS 1.3 protocol with advanced encryption, akin to what major financial institutions use. Additionally, security protocols ensure that each message exchanged is unique, making it virtually impossible for hackers to intercept and replicate access credentials.
Let’s start with the basics. Can you explain how virtual keys are handled in smart locks, particularly concerning authentication and authorization?
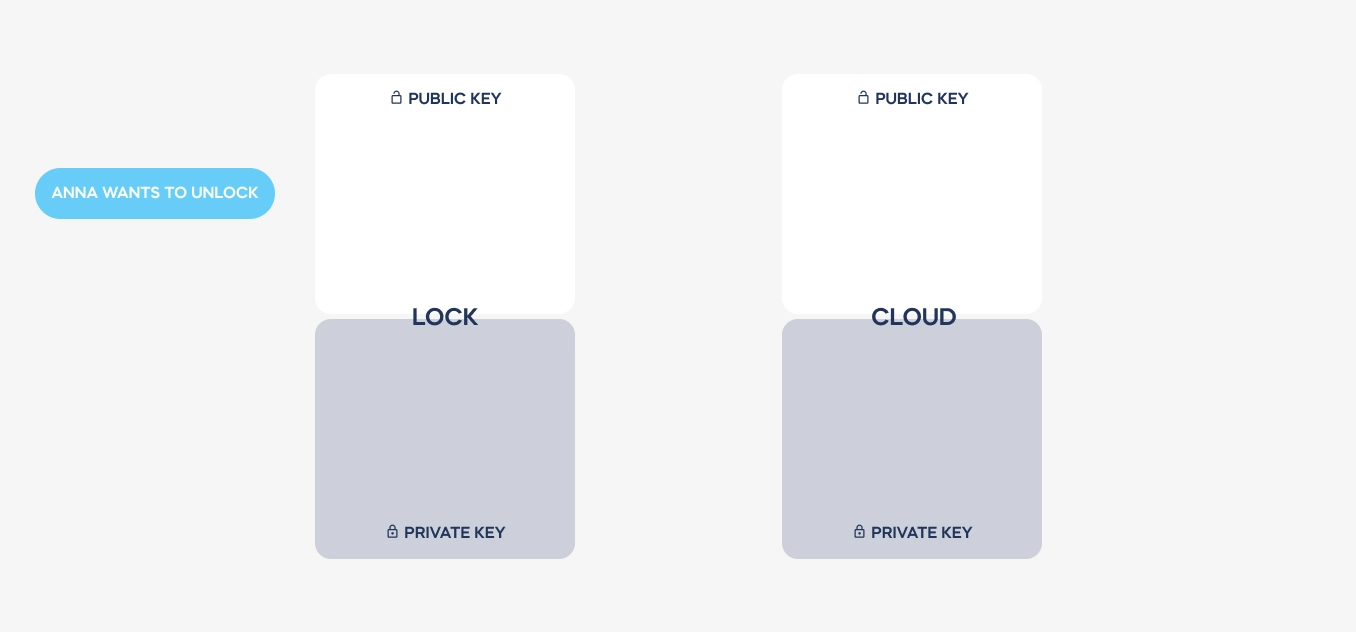
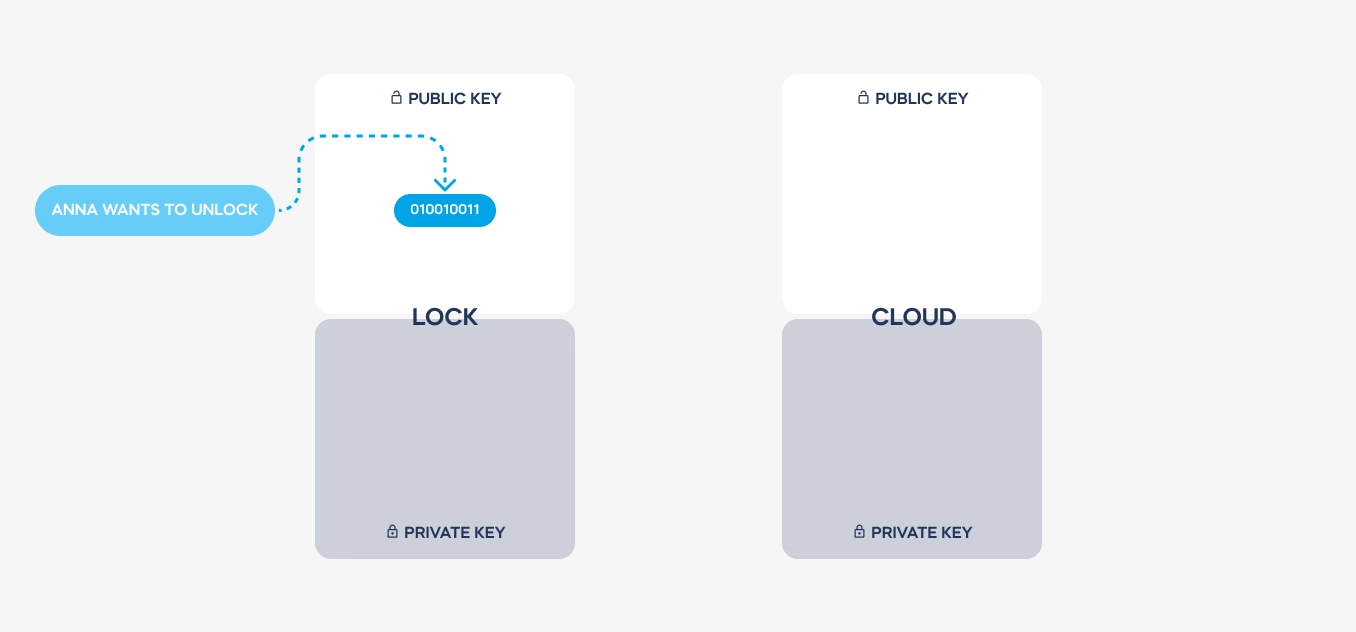
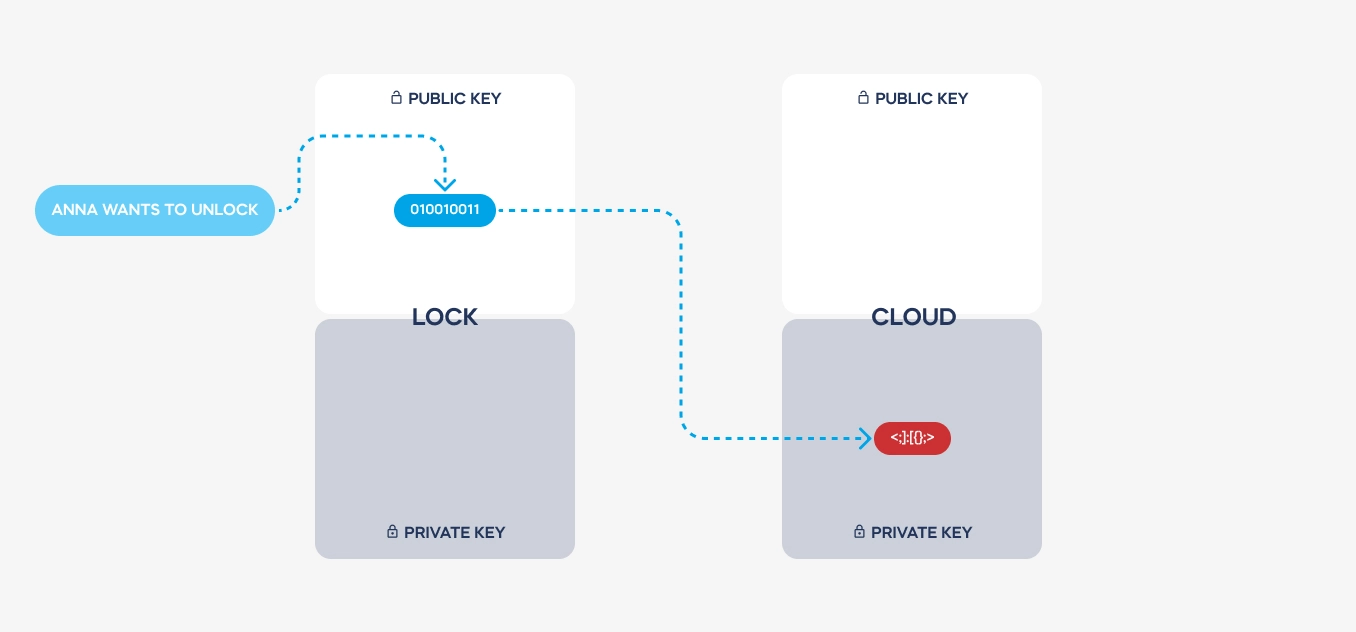
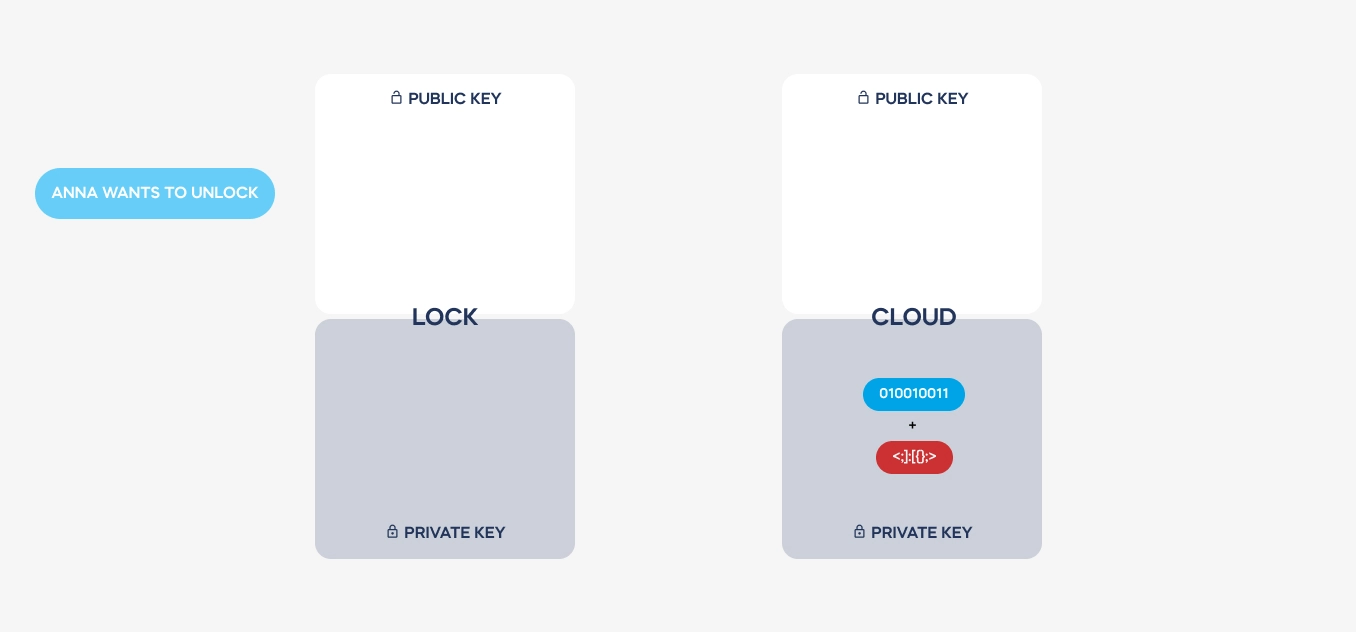
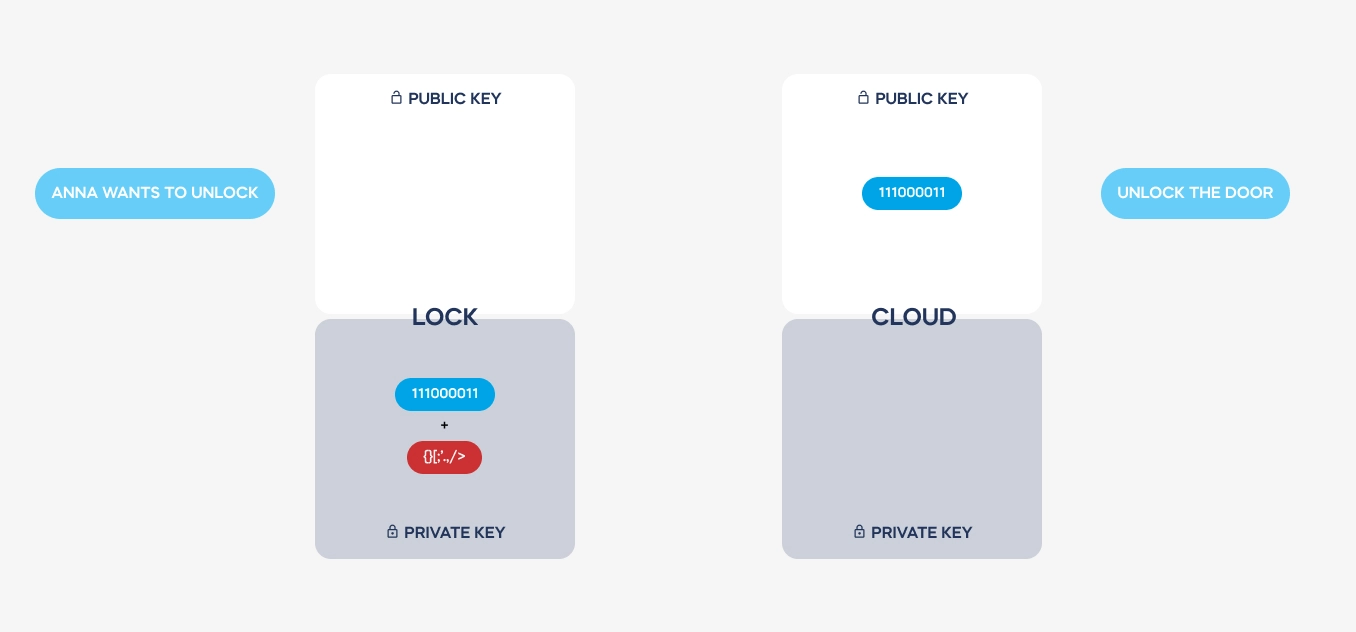
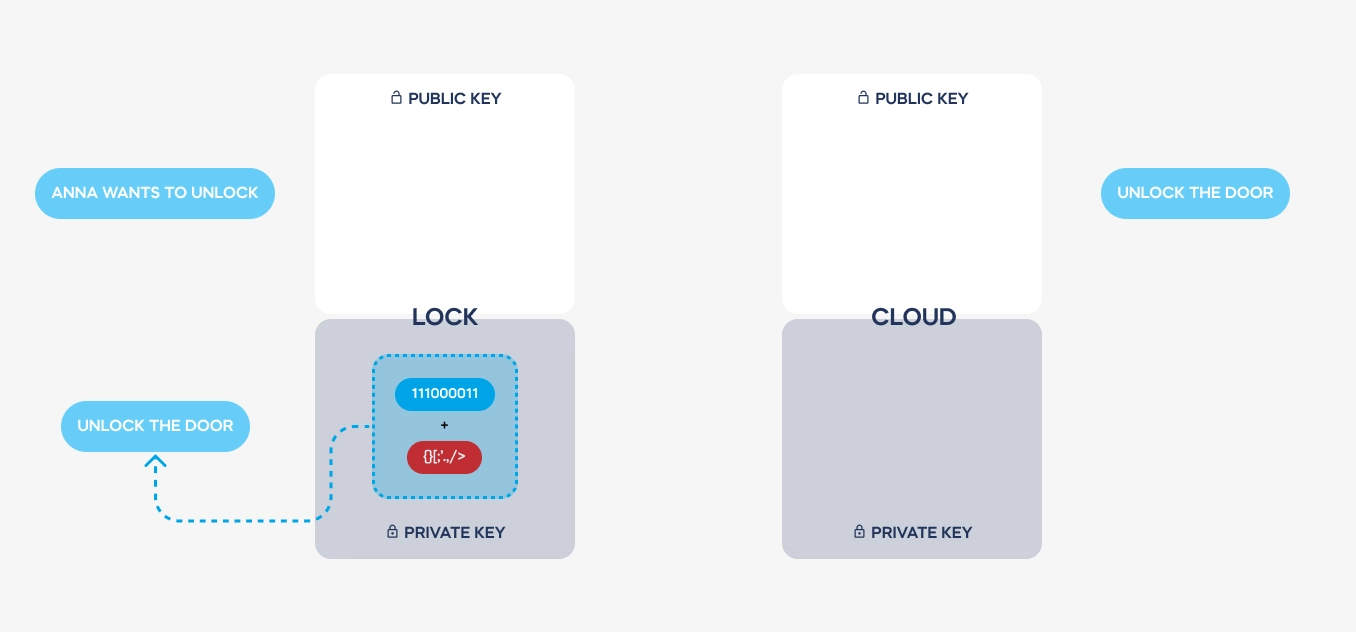
GC: Certainly. In smart lock systems, virtual keys are essentially digital representations of physical keys, granting access to authorized users. To establish a connection with a smart lock, a user’s device must first authenticate itself through a cloud-based system and download a security certificate, which is later authenticated by the lock. This certificate dictates the level of access granted to the user, whether it’s permanent for the lock’s owner or temporary for a visitor. These digital keys are encrypted using asymmetric encryption, ensuring their security and authenticity.
That’s fascinating. Could you elaborate on how asymmetric keys work and how they contribute to the security of smart locks?
GC: Asymmetric encryption involves the use of two complementary keys: a public key and a private key. These keys are issued only once during the setup process and are used to encode and decode messages between devices. Importantly, the private key never leaves the device, ensuring that it remains secure. This encryption scheme, combined with stringent authentication protocols, ensures that communications between devices are encrypted and single-use only, significantly enhancing security.
Moving on to the cloud aspect, there’s often concern about the security of cloud-based systems. How does Tedee ensure the security of its cloud infrastructure?
GC: Tedee leverages Microsoft’s Azure Active Directory B2C service, one of the leading cloud solutions globally, to power its cloud infrastructure. By partnering with a reputable provider and undergoing thorough security testing, we ensure that our cloud environment meets the highest standards of security and reliability. Additionally, data stored in the cloud is anonymized, and access is tightly controlled, minimizing the risk of unauthorized access.
Finally, what are some common risks associated with smart locks, and how can users mitigate them?
GC: Smart locks contribute to security by eliminating the risk of losing or having keys copied, etc. They also address concerns related to living in a home where the lock hasn’t been changed and someone else rented it before you, significantly enhancing the sense of security. However, there are still risks to consider, primarily stemming from human factors. The most significant risk is the compromise of Tedee account credentials, which could grant unauthorized access to locks. Users can mitigate this risk by using strong, unique passwords and regularly scanning their devices for malware. Additionally, it’s essential to practice good smartphone security hygiene, such as locking devices with PINs or biometrics. Ultimately, a holistic approach to security, encompassing both hardware and digital aspects, is crucial for ensuring the safety of smart lock systems.
Thank you, Grzegorz, for sharing your insights and expertise on smart locks and digital security. It’s been enlightening to learn about the intricate mechanisms that safeguard our homes.
GC: My pleasure. If anyone has further questions or concerns, feel free to reach out. Stay safe and secure.
Read our complete guide to smart lock security, here >>