Your cart
Your cart is empty
- No products in the cart.

Tedee GO

Tedee GO2

Tedee PRO

Tedee Bridge

Cylinders

Adapters

New Tedee Keypad PRO

Door Sensor

BleBox smart relay module

Tedee Dry Contact
It’s time to give your front door a whole new meaning.
Enable new ways to enter, protect, and share your place.
The smart lock and your smartphone are all you need to get started.

“Tedee GO: CHIP.de test winner – best smart lock under €150”
“Finally a fast, reliable and enduring connected lock.”
“What immediately stands out is the attractive, compact design.”
“Chic and slim knob design. Powerful, quiet, and enduring integrated battery.”



This discreet device is installed on a door lock inside your property. Smart lock works by controlling your existing lock cylinder like seamlessly rotating a key. Your hardware stays intact, and you can also conveniently unlock it like a traditional door using a key.
Just like a computer on your door, Tedee smart lock simply connects to the internet and your other devices. You can lock and unlock your door with your smartphone – even from the other side of the world.
This combination of the locksmithing heritage and tomorrow’s technology
offers new possibilities of what your door can be.


Forget looking for your keys in a rush or with your hands full of groceries. Your home will be ready to welcome you with an open door.
Imagine how simple leaving, locking and re-entering your home could be. Tedee is the perfect concierge for you and your family members. Elegant and discreet, it locks and unlocks your door as you intend.
Automatic locking
Automatic unlocking

What if handing over your keys worked like an e-mail? You can create and send your extra “key” in the app when unlocking your door with a smartphone.
Take control of your home. Choose how anyone can use the virtual keys and when they’re active. If you want your keys to only work certain hours of the day or specific days of the week – you can make that happen.
Three user types
Precise access settings
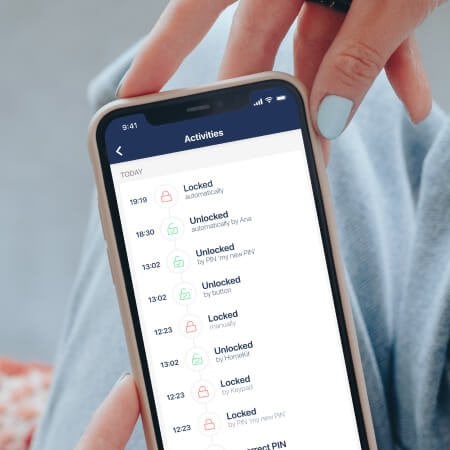
Are you curious to know what is happening at home? Tedee gives a detailed history of who has accessed your place and when -even in real-time. Our technology ensures your home is safe, secure, and constantly easily monitored.
Are your kids back from school? Are you expecting a guest? Use the alerts function to view your home at a glance on your smart device.
Push notifications
Live activity logs

Did you know that traditional keys were first used 6000 years ago? Since then, we’ve moved on. These days, traditional keys are not enough.
Tedee is now the future. Secure your lock like never before. Connecting your Tedee to the online cloud brings high-tech protection to your door, guarding it with secure digital technologies similar to internet banking.
Cloud-based security
It’s satisfying when you find a refined product that contains a ground-breaking function. Simple yet life-changing. From Tedee’s luxuriously discreet design to the gentle movement: experience how key-free access can enhance your life.

Choose long-term sustainability. Your Tedee unlocks the path to a circular economy and more conscious protection: from renewable materials to limiting resource consumption.
Recyclable aluminium
No more changing locks
Long-term product support
The end of extra keys


Enjoy the most superior smart lock on the market. Sleek, quiet, and with a unique look.
Works with Tedee-ready cylinders and adapters.

An affordable, sleek, do-it-yourself smart lock – now even quieter and more efficient.
No accessories needed for installation on double-clutch Euro-profile cylinders.

Imagine your home had an on/off switch. Now use your smart lock this way – launch automatic actions when you go out or get back.
Start your vacuum and disable heating when leaving. Upon arrival, be greeted with music, lights, a kettle, and other smart home devices. Your Tedee smart lock enables automated smart home scenes that you’re going to enjoy.


+ more than 15
smart home systems
Start smart hosting easily. For your and your visitors’ comfort.

Your cart is empty



