Is smart lock secure?
Connecting a door lock to the internet does seem scary. With such new devices as smart locks, doubts are natural. But isn’t that the case with all new technologies? Wasn’t that a case with online banking or contactless payments?
But when we break down our doubts, address them from the start, and understand the technology involved, the magic happens. And who knows? Maybe smart locks will become your next trustworthy companions.
Key points
- How are smart door locks safe?
- Can smart locks’ protection be compromised?
- Should I trust smart locks?
Contents
- Introduction: will this text help you?
- Physical security: offline mechanics
- Digital security: where the smart happens
- Risks: what do you need to know
- How to choose a secure smart lock?
- Conclusion: can you trust smart locks?
Introduction: will this text help you?
You probably have discovered smart door locks through their groundbreaking additional features: auto unlock, access sharing, auto lock, remote access, or smart home integrations. Maybe you have seen how your friend unlock the door with one command, said to a smart speaker, or a pin code.
Then there were questions coming to mind: can a smart lock be hacked? What if I lose my phone? What does a cloud even mean? If this thing unlocks automatically, can it simply unlock itself when I’m not there?
You’re wondering if unlocking a smart lock with an app protects your home enough. Are smart door locks safe?
It is important you have these doubts – we have had them too. Then we addressed the security from the start of making our device until both digital and mechanical security experts on our team were satisfied with their solutions. And we’re all testing each version for months before our smart locks enter the mass market. After years of development and intensive testing, even external security authorities have approved our solutions. Thousands of tedee smart locks are used every day by more than 10 000 people daily, more than 5 million times per year. Now we all use tedee at our smart homes. Many of us have even installed it at our parents’ homes. If you recommend something to your mother, it better be good.
Why you should trust us
We are a team of mechanical engineers, including PhD specialists in technical sciences and cybersecurity experts experienced in work for the world’s biggest brands, like Microsoft. This unique combination provides us with a complete view of the smart lock. Inside our company, we have a thorough knowledge of every part: from tiny details of an electric mechanism to state-of-the-art programming.
Tedee is co-founded by two companies.
GERDA, a renowned lock hardware company with over 30 years of experience, has mastered engineering and lock construction. We are aware of the responsibility of creating a equipment that protects your home – and GERDA lock makers have one of the best know-how on the market, protecting millions of European households. GERDA is also a maker of the now-iconic round cylinder that has revolutionized the widely available high-security locks with a new type of extremely secure keys. You can see a short video about this cylinder here.
The digital security part of tedee’s operation was provided by Predica, the largest independent Microsoft Cloud Services partner in Europe. It is the only company in CEE certified as Microsoft Azure Expert MSP and is attested with ISO/IEC 27001 quality norm. Predica’s expertise covers creating and maintaining safe digital solutions for Santander Bank, Maersk, or Jabra. You can see Predica’s offer here or read their blog. Yes, these are highly specialized services for the largest companies in the world. You need to know about Predica’s expert knowledge of Microsoft products and the team of experts who might have built many solutions you’re using even right now.
Fusion of these two worlds allowed tedee to be officially certified by the Independent IT-Security Institute AV-Test. It has tested and proven tedee as secure and granted it with an approved smart home product title. You can read a thorough report from AV-Test here.
How we will help you
It all seems complicated, doesn’t it? That’s because most smart locks are much more than a “door lock with a remote”. They connect the physical with digital protection, two areas using highly specialized solutions. Here, we’ll divide these technologies into main parts and analyze them step by step. We will start with a physical foundation of a smart lock as front door hardware. In the second part, we will dive into digital security. In the end, we will overview how smart locks work in practice to highlight the high-risk points you need a full picture of.
Prepare for a couple of professional terms – like communication protocol or asymmetric keys – but don’t worry. There will be analogies and infographics that we hope will make them approachable. The ways these technologies interact with each other is another level of technicalities that we do not need to cover right now.
I hope these main aspects will give you enough background to make an informed choice and decide if you wish to trust a smart lock yourself. Because putting it on your front door is not just about convenience – it is to make you feel safe.
Physical security: offline mechanics
A smart door lock has no mechanic impact on the security of your door hardware. Inside your door, it works simply as an electric tool for rotating your cylinder, as if a physical key. From the outside, it’s not even visible, and you can always unlock it with a standard key.

Before we get to digital specifics, let’s start with an analysis of its mechanic properties – and if it is a secure device even in its offline “flight mode.”
Cylinder or adapter?
A proper mount of tedee on your traditional lock is necessary to control your door with smart technologies. Many smart locks on the market offer either installation on a dedicated cylinder or an adapter suited to your lock type. After successful installation, these have no impact on everyday use. But are these solutions any different in terms of home security?
 |  |
Smart lock installed directly on a dedicated cylinder |
Smart lock installed with an adapter attached to an existing cylinder. |
When changing a cylinder to a compatible type, ensure the new hardware is certified with a trustworthy security class. At tedee, we offer GERDA cylinders, attested with Class 6, and M&C cylinders with SKG*** rating. Made by these reputable European companies, each with over 30 years of experience, ensure certified anti-burglary protection, over 100 000 possible key code combinations, durability, and drill and lock picking resistance. These do not decrease your door’s security and are proven protection when properly installed. Two types of security standards allow you to match theirs attests to your door. It may be required for your lock’s highest standard of protection or property insurance guidelines. We have created a thorough guide to selecting a suitable cylinder for your door here.
If your door requires an SKG class 3 of burglar resistance hardware, you must choose an SKG*** (three stars) certified cylinder. It’s also a guarantee of pull resistance and a minimum of 5 minutes of resistance when tried to break in.
With an adapter, your lock stays exactly as safe as it was. If you have a less popular mechanism, a specific type of door or its manufacturer requires a specific certification of a cylinder, it is an easy and secure way to go. Adapters are also a great way to use a smart device when you simply do not want to interfere with door hardware – in a rented flat or office space. These do not require you to replace cylinders.
If you wonder which installation method should you choose, this article may be helpful. Both ways, smart door locks’ installation is easy, with just a screwdriver, however there may be some additional requirements to replace hardware on your door.
Can a thief destroy a smart lock?
Remember that a smart lock is installed inside your home. From the outside, it is not visible nor accessible – including for getting stolen. Hence mechanically, it is not possible to influence its operation. The distance between the outside of your door and the lock inside reduces the risk of electrocution.
As we said before, a smart lock doesn’t reduce the physical home security nor makes your home vulnerable to burglary, even when it’s offline or off. In a very unlikely event it breaks, battery life ends, or the internet connectivity goes off (or you lose your phone), your smart door lock works just like a classic one. From the inside, you control it manually, using tedee as a doorknob. From the outside, you lock and unlock with a standard key. As long as by design you can unlock tedee without a key, it is advised you carry its single, flat key in your wallet, to gain access at any time.
Main unlocking methods | |
| From the outside | From the inside |

Nothing. It’s automatic. | |

Mobile app | 
Button |

Smartwatch | 
Doorknob |

Keypad | 
Voice assistant |

Traditional key | 
Online portal |
Keys included in your tedee cylinder box are virtually impossible to make a copy and forge by unauthorized persons. Only GERDA and M&C-certified partners can make extra keys using a code card supplied with a cylinder. Dedicated cylinders possess over 100 000 key combinations.
That also means that however smart lock does not impact mechanical security, your cylinder can always be prone to decoding, drilling, or breaking. To protect your lock as much as possible, make sure to select a proper length cylinder and use it with a protective escutcheon. It is valid not just to smart lock setups – these are guidelines important for every lock.
However, remember that a smart lock is not recommended for high-risk property protection in places such as vaults or secret archives, even protected with security cameras. There are specific products and technologies on the market designed specifically for such setups. It would be best to consult that with your security team, as local limitations or maintenance may be involved.
Why metal key is not the safest option
The traditional key symbolizes control – it allows you to grant access only to those, who keep it. But a piece of metal is not always the safest option.
Do you have complete trust in all persons that have ever touched your keys? Have you ever borrowed them to a redecoration team, neighbor watering your plants, temporary employee, or short-term rental guest?
Renting an apartment? Who knows who had lived there before you – and if they gave back all of their keys. Are you sure your landlord does not visit when you’re not there?
Are you really sure your locked, key-protected door is safe?
When handled improperly – which is hard to control – or the key is accessible to numerous users, it can get copied, lost or stolen. Whenever your trust is less than 100%, your locks should require changing the cylinders – which are just as prone to breach, again.
It’s natural to be anxious about “digital keys” and how safe they are. With the latest technologies and multi-level mechanisms, your smart lock can protect the access much better than a piece of metal. In the next chapter, we will get down to cybersecurity and digital methods of protecting your locks.
Digital security: where the smart happens
The only thing that protects access to a traditional lock is a metal key. In comparison, every single use of tedee triggers a multi-step and multi-level procedure of checking whether the user is allowed to do so, provided by an online cloud. The procedure is like using the ATM or paying with a credit card.
What is a cloud? What does it mean that smart door locks works through a cloud?
You can think about the cloud simply as the web. A cloud stands for a security system operating on an online server. Imagine as if your door lock works like online banking. It uses complex security software that authenticates your identity and permissions with the latest security technologies. The cloud sends a validated signal to your lock if approved, allowing it to unlock. The cloud allows for more advanced technology than any device on its own.
Also, outsourcing some of the lock’s operation online allows integration with cloud-based smart home systems, such as Google Assistant, Apple HomeKit, Amazon Alexa, Homey, and others. Whatever system you use to control your tedee, the cloud-based security procedures stay the same.
Why should I unlock my door through a cloud?
“The lock provides an easy-to-use experience. The cloud provides the safety belts” says Tomasz Onyszko, Predica Co-Founder and CTO, author of onyszko.com. Later he describes how a cloud aspect is created: “In cyber-security, there is a concept of the “threat model.” To build something secure, you start to think about all possible ways things might go wrong.”
It means the hacking issue would be the first and foremost matter ahead of cloud engineers: “cloud vendor has tons of people thinking, “what could go wrong.” They apply all possible fixes for it to not go wrong. They care to make it hard for, for example, a lock to make mistakes.”
Worrying that someone will “hack the cloud” […]
is a wrong problem to worry about.
“Fear about the safety of the cloud is common, but the cloud environment is more secure than anything we can build on our own. If you are not aware, many banks nowadays run in the cloud. If banks trust the cloud and people trust them with their money, why should it be different in the case of a lock at your doors?” he asks.
Imagine smart locks without a cloud: electronic devices turning your door lock, controlled with Bluetooth app. They can be paired and secured, but all security features would be implemented inside a lock and a smartphone.
This is a scenario for a tragedy: all smart home security would be implemented inside a widely available app, and all lock’s protection – inside a widely available product. With both sides of static technology widely available, it is just a matter of hacking experience. However, smart home technology has a solution for this.
This is why it’s important to engage with a system placed somewhere else – an outsourced environment for protection procedures. As the cloud-based security part of tedee is provided by Predica, which supplies Microsoft Cloud services, it works according to the ultimate security and reliability standards. In addition, our cloud solutions have been tested by an external security testing company Securing (https://www.securing.pl/), which specializes in verifying the digital protection of banks and institutions.
We often call these solutions “digital keys” because they provide unique, impossible to copy protection that is issued only to authorized persons. We will focus on what this technology is made of to further present how they protect your smart lock.
“Fear about the safety of the cloud is common, but the cloud environment is more secure than anything we can build on our own. Worrying that someone will “hack the cloud” to open the smart lock is a wrong problem to worry about.” sums up Onyszko.
Can a smart lock be hacked?
Let’s start with something it all won’t work without: wireless communication between your smartphone, smart lock, and the cloud. Your setup may involve a smart bridge plugged into an electric socket. This is the best friend of smart locks and plays the same role as a phone, but it is stationary, connected to Wi-Fi instead of mobile data.
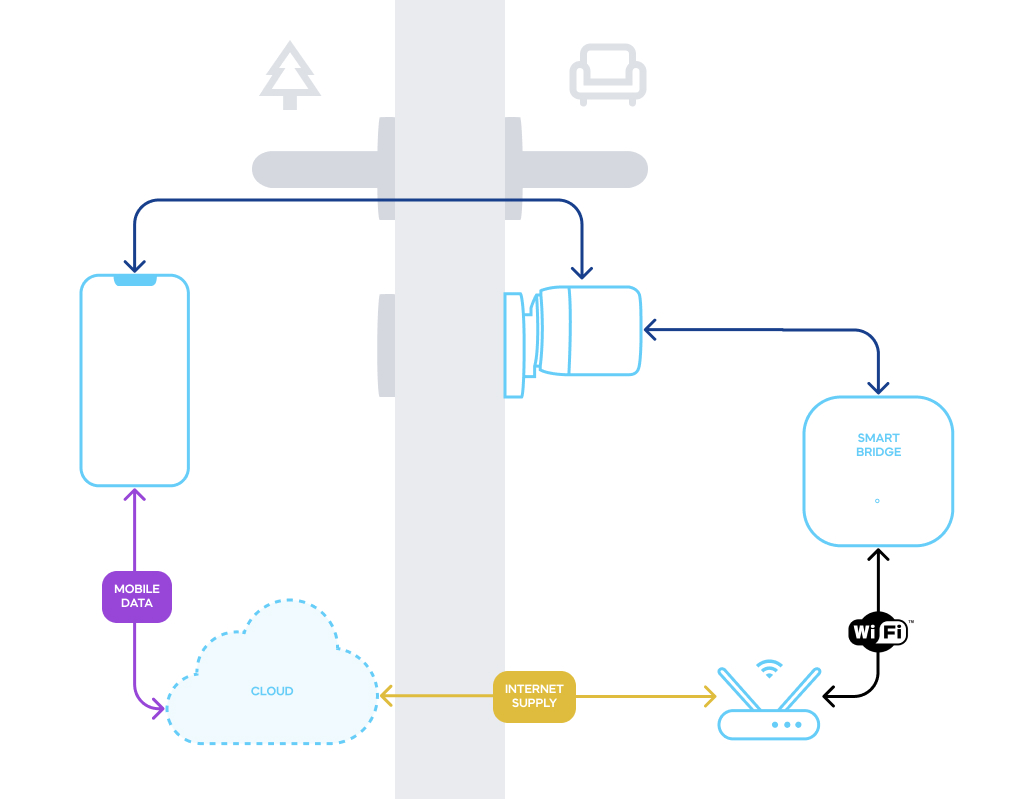
At first glance, these seem ordinary – and breachable on so many stages. However, none of these connections is a simple link. It works on not just single-contact messages but a series of mutual enquiries. It makes data exchange more into dialogue than just a greeting. These sets of strict rules of the message exchange are called communication protocol. This is a multi-step procedure, but the connection is aborted if any process step fails.
tedee uses the latest TLS 1.3 protocol with a 256-bit security key. These may sound undecipherable – and they are – but you should know these are technologies that protect the payment services of the world’s largest companies and online banking. Now this type of protection is available to protect your smart home security.
Security protocol: single-use messages
But what does this mean in practice? In short, this equals that the encryption system registers every message sent and received – and it will never accept the same message again.
For example, let’s take a situation where a hacker intercepts all communication between devices when opening the door to copy it and use it themselves. Suppose the hacker has intercepted message number 100 and wants to send it again. But the smart lock will require message number 101. The message that the hacker copied is useless now, and the action will be rejected. To gain access in this situation is impossible, and cyber attacks are inefficient.
“Virtual keys”: how to handle them
Your smart locks stay connected only to your phone or smart bridge via a wireless Bluetooth connection. No other device can connect to a smart lock. The first step of establishing a connection session is authentication and authorization of the user’s device. AV-Test report described our Bluetooth solutions as “encrypted according to state of the art and thus secured against attacks from the surrounding area.” Let’s see how it is protected.
| Who are you? | What are you allowed to do? |
| Authentication | Authorization |
To connect to a smart lock, a user must connect to a cloud and download a security certificate later authenticated by the smart lock. Your smartphone or smart bridge are not required to connect to a cloud at every smart lock’s use. So a temporary lack of mobile service or power outage will not impact the lock’s use via Bluetooth.
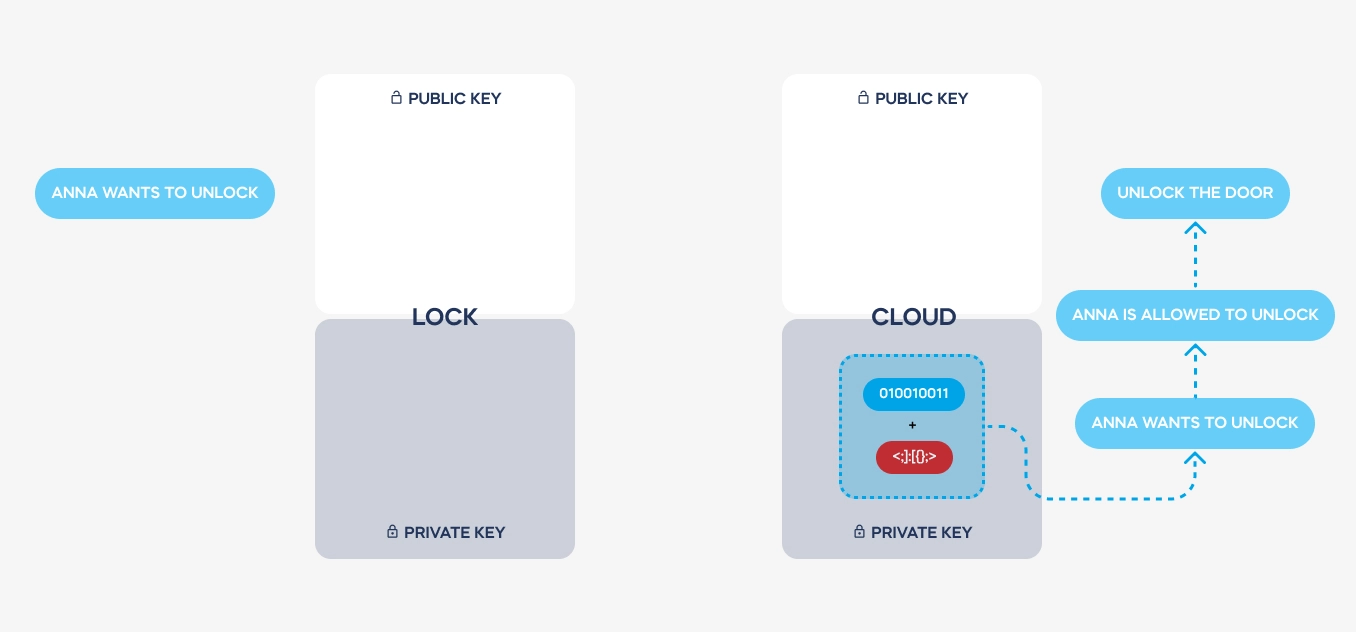
A certificate is valid according to the access granted to a user: permanent to a lock’s owner or administrator, temporary to a visitor etc. It is enough for smart locks to renew their certificate once every 7 days. It is signed off by an external, Microsoft-supplied system, powering access control and user permissions, making a certificate impossible to forge. These are your “digital keys”. For you to get or share them, asymmetric encryption is used.
Asymmetric keys
Communication between devices is encrypted, which means that communicated signals are not understandable to any other party. But didn’t we all hear about code-breakers or the famous Enigma? These are a thing of the past. tedee uses 256-bit asymmetric key encryption, which is virtually impossible to forge. Let’s dissect how it works.
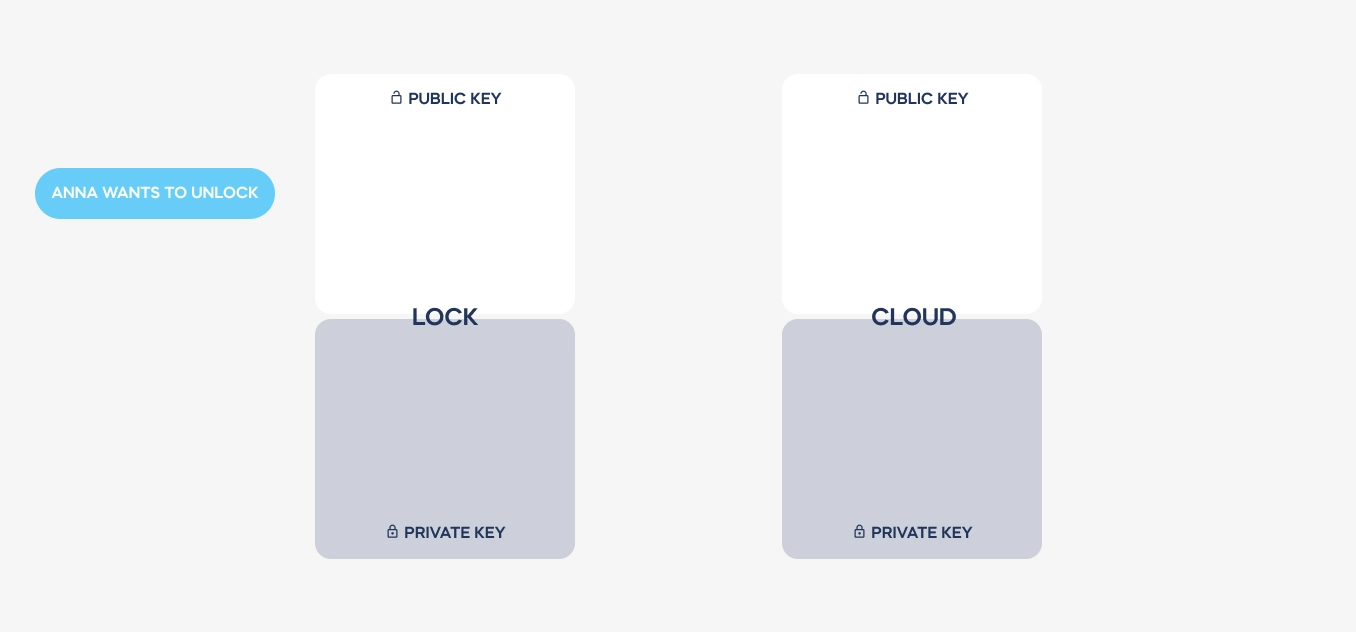
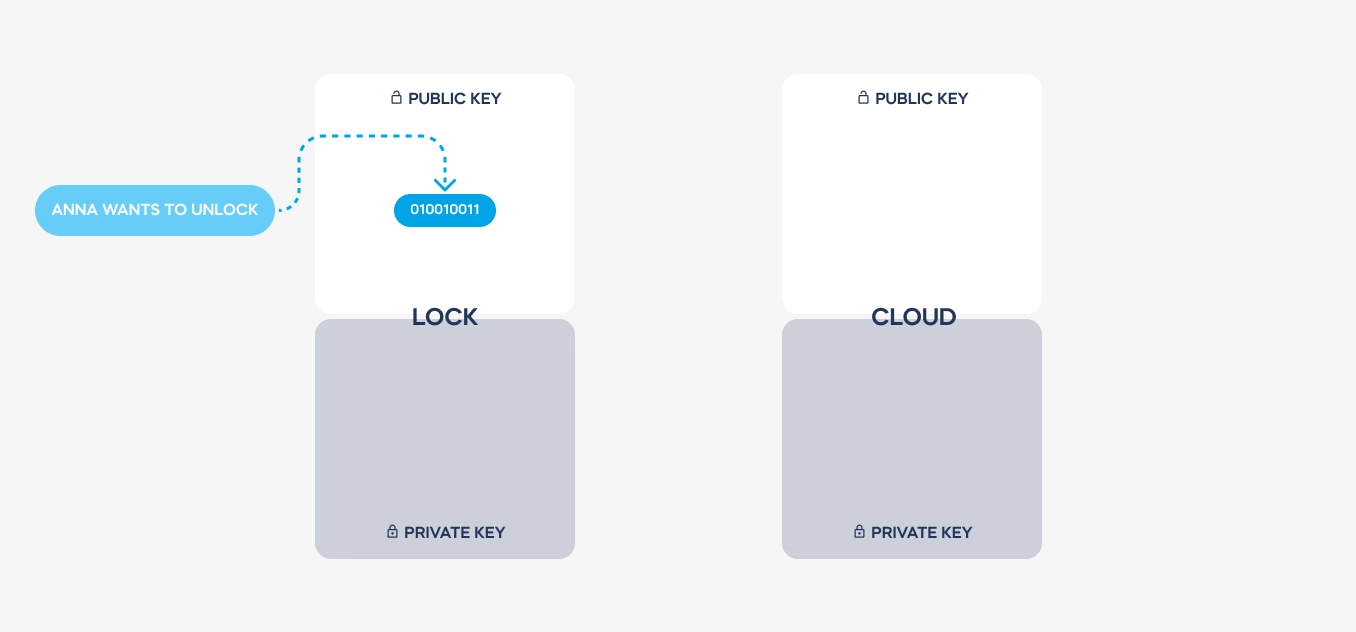
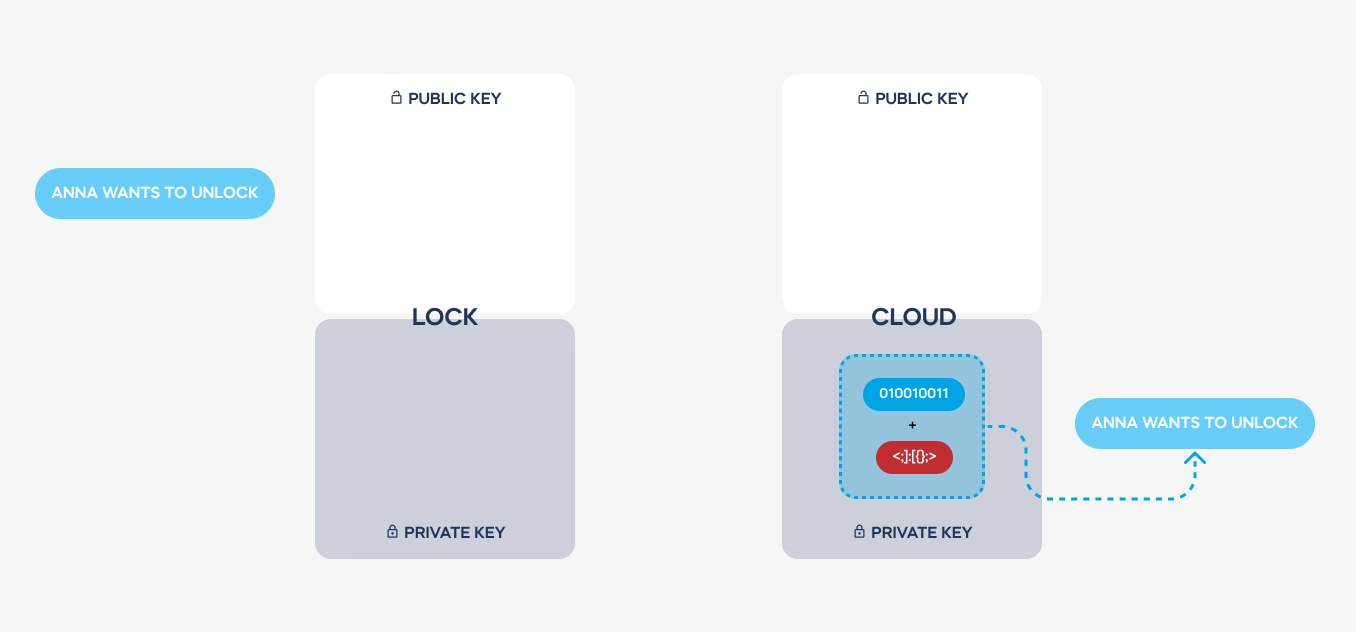
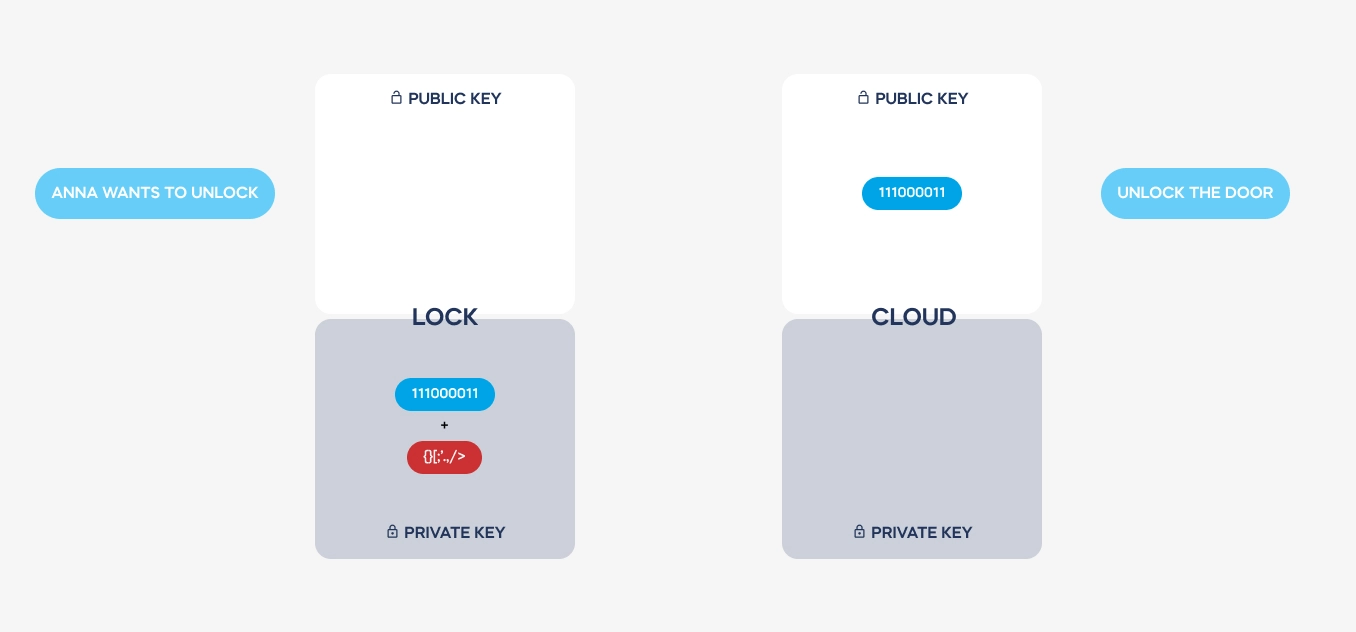
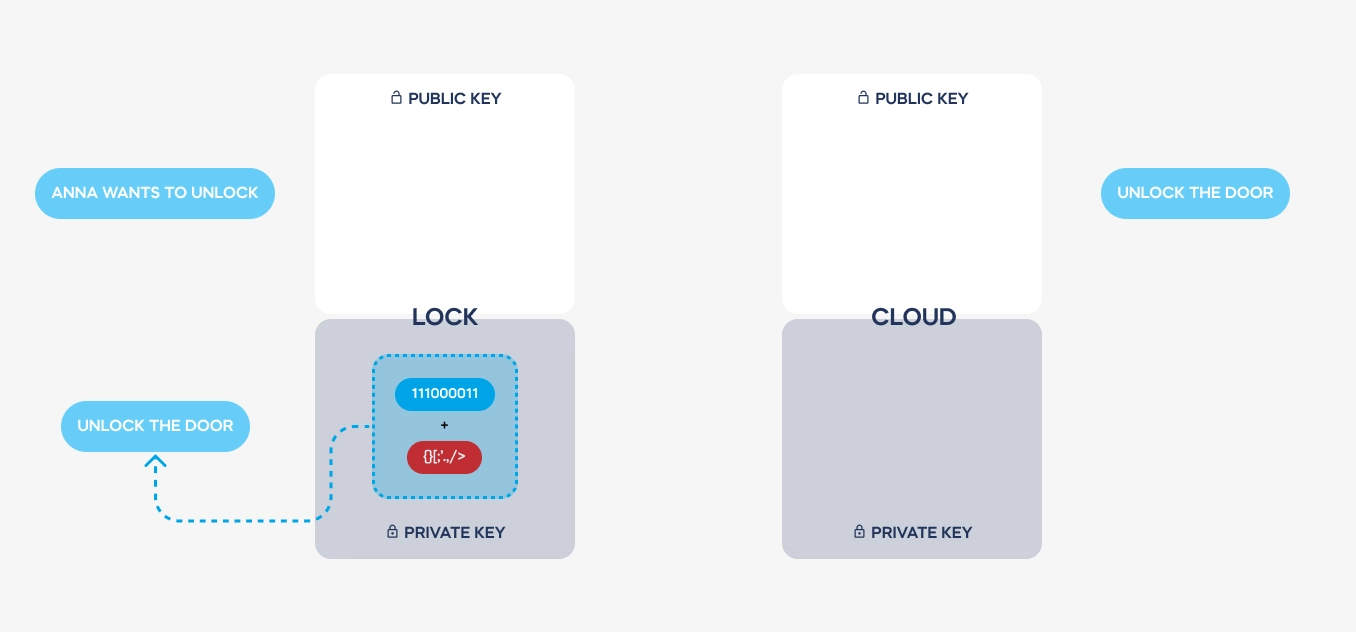
Imagine two devices that need to communicate with each other securely. Both have been provided with two complementary encryption keys: public and private.
| Key used for communication
Sent for authentication | Key used for authentication
Never leaves the device |
| Public key | Private key |
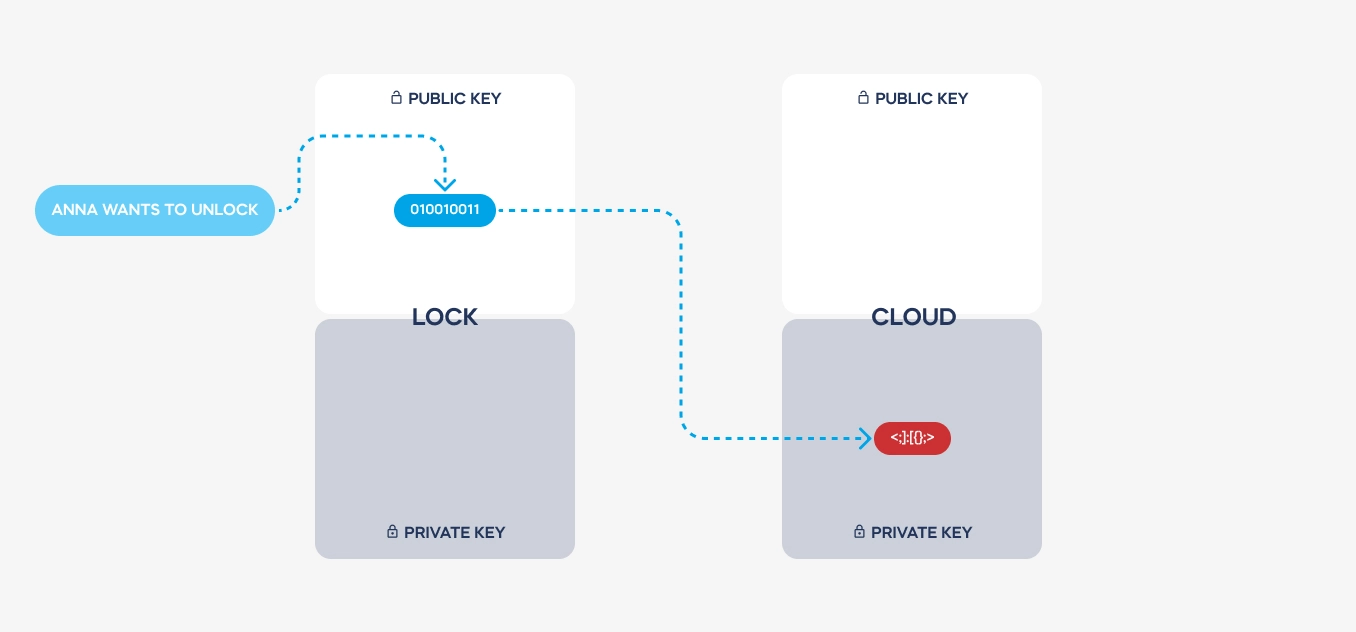
Pairs of keys are issued just once, producing a smart lock or pairing it with a tedee account. Both keys are always required to decode a required message. – but private keys are never transmitted. There is no way to steal it from a Bluetooth or Wi-Fi connection.
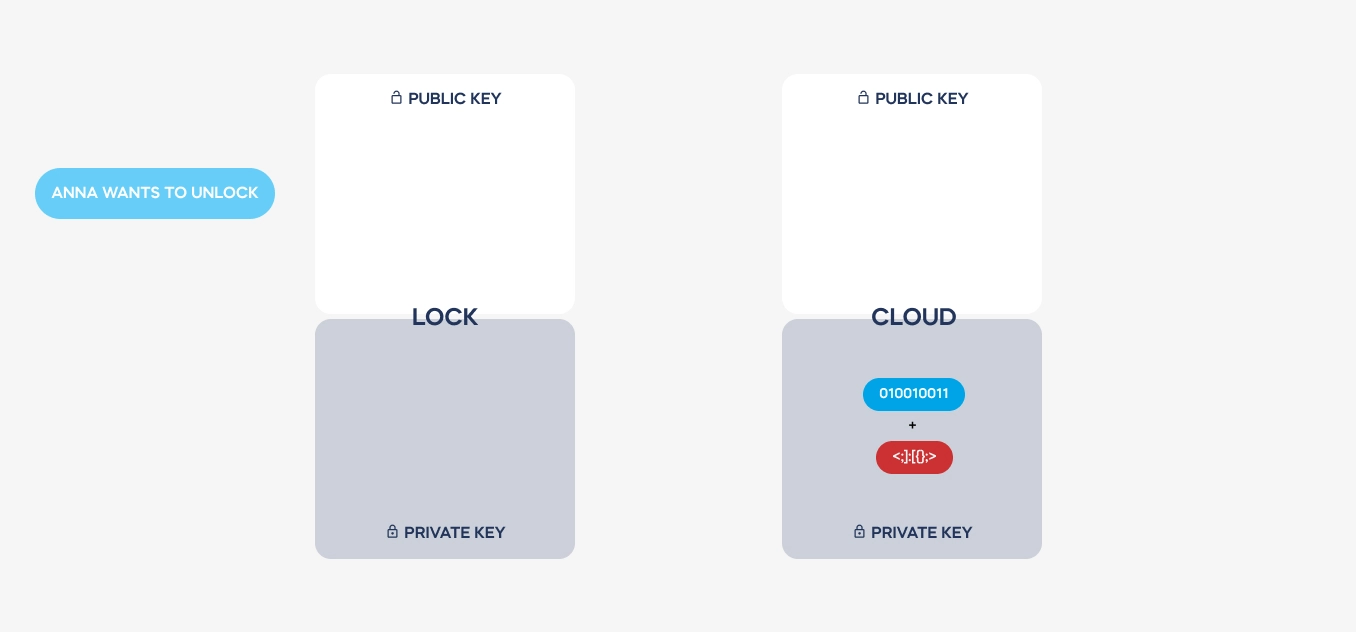
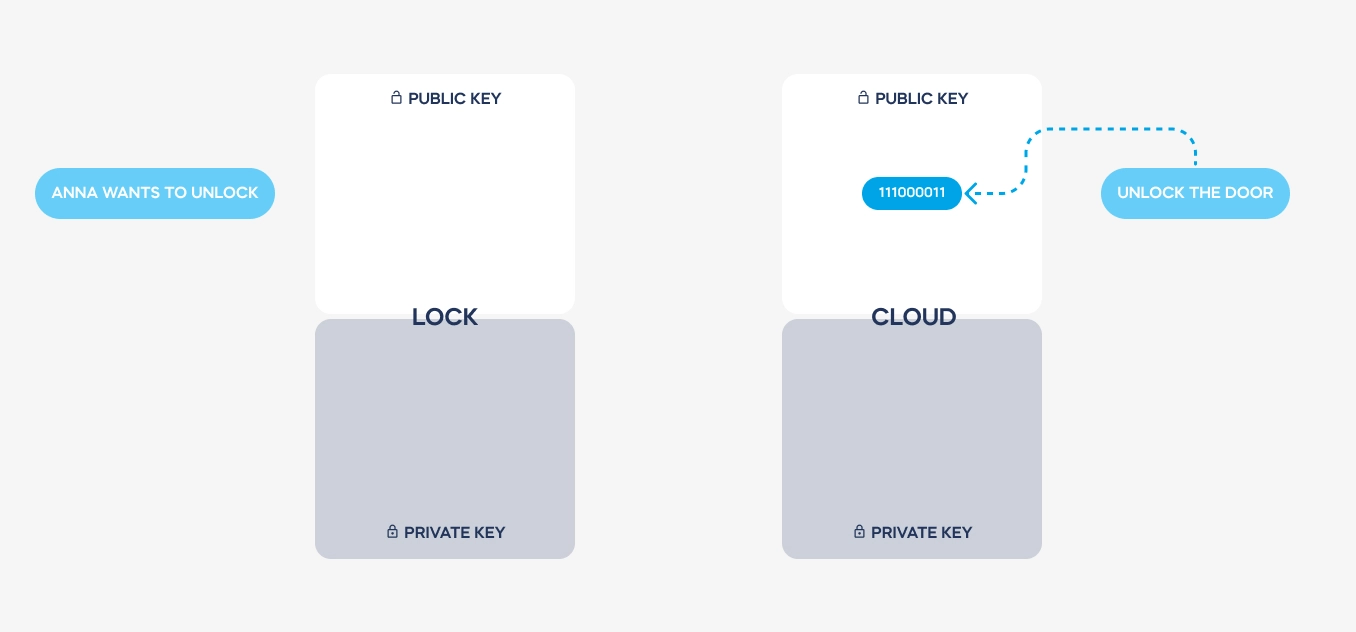
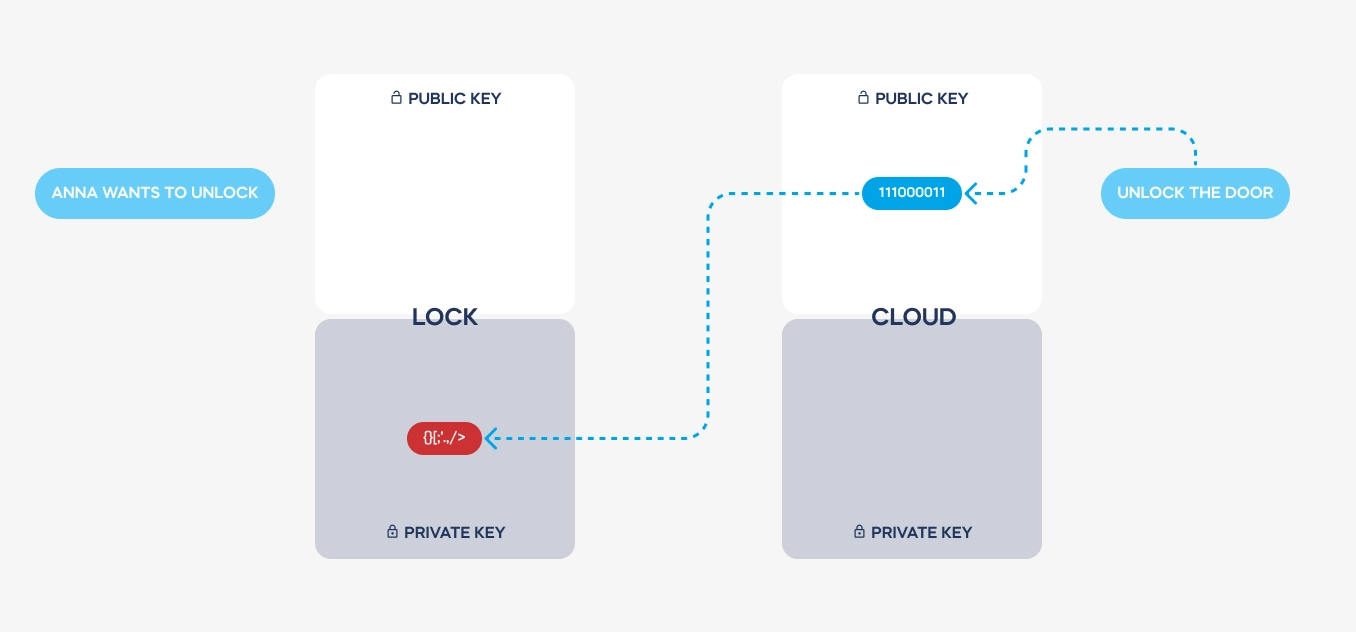
Here is a simplified illustration of how a message is transmitted and coded. See how the private keys never leave the devices used. These are stored on dedicated electronic elements, protected from any access.
Both keys are used to send back the decoded message from the cloud to a lock. Hence, the authentication is always safe, encrypted, and single-use only.
Is the cloud secure?
First of all: tedee is powered by Microsoft’s Azure Active Directory B2C service, one of the world’s leading solutions. Our synchronization with Microsoft is supplied by tedee co-founder, Predica.
These are important facts because of at least two reasons.
External data storage provides the highest level of home security, unattainable for smaller or local entities. Our systems are not stored by a smart home company. These are stored at one of the safest security solutions in the world. Unless your account’s login and password are leaked, a hacker would need to break into Microsoft servers.
Third-party cloud software works on anonymized data. Access to those is protected, and there is no physical way to read it and link it with a particular device – even by tedee employees. Keys and user accounts are not stored on the same server. This means that even if the information is leaked, personal data would still need to be associated with the database’s keys – otherwise, they’re useless.
Risks: what do you need to know
tedee uses the most up-to-date solutions – its firmware and app are updated dozens of times per year, and our hardware is security-certified. Smart locks can be considered to provide greater security than traditional locks. However, it is valuable to know more about how these work in practice and be careful.
Auto-unlock: perfect for error?
No matter how convenient it is, automatic unlocking does feel like an error-prone feature. We knew that from the start and made a solution that protects us once and for all.
Without authentication of “digital keys”, tedee stays locked – unless you press its button from the inside. Remote unlocking always requires a multi-step process, ignited by a Bluetooth-connected smartphone, keypad, or a cloud through a smart bridge. It is impossible by design for smart locks to unlock without an operation launch.

In addition, automatic unlocking uses another layer of checking if you’re near. It includes two zones circled around your smart home compared to your present location. The lock never unlocks by itself – it requires you to leave the “out” zone, then get back to the “in” zone, and come to the door in less than 20 minutes. That’s when the lock starts detecting if you’re near but will not unlock unless you’re up to 3m away.
You can read a full guide to automatic unlocking configuration here.
What is the weak point?
It’s easy to say for a technology company, but honestly: it’s a human factor. tedee uses the latest digital security solutions provided by the world’s best providers from the side of technology. Both its mechanism and software have been certified by reputable organizations. Additional smart features were designed precisely to use all in their power to work securely. So far, years of operations at thousands of households may have caused single issues, but not security breaches.
tedee account
The only way for an unknown person to access the locks is to steal a tedee account login and password credentials. This may be caused not by tedee systems but by viruses or malware logging characters on your smartphone or computer.
Remember to regularly scan your device with up-to-date security software from a trusted provider.
Make sure your tedee account uses a unique password composed of at least 8 characters: small capital letters, digits and symbols. It is not available to use plain text passwords. Ensure the emergency e-mail for resetting the tedee account uses a secure password and is protected with an associated phone number.
Smartphone protection
After a tap in the tedee app or a widget on your home screen, the smart lock unlocks in regular manual operation. To do that, you usually – and you should – unlock your phone first, with a PIN, key code, face scan or fingerprint. It is enough to log in to your tedee account once, but that requires elevated smartphone protection.
In case of any doubt, you can log out of your tedee account – for example, when it’s easy to lose a phone when travelling.
Mobile widget
However, some smartphone operating systems allow selected widgets without unlocking your smart devices. Using the tedee widget will enable complete control over your smart lock if your phone gets lost or stolen – without PIN, face or fingerprint scan. Consider this a risk factor to mind, and maybe a feature to pass.
How to choose a secure smart lock?
Smart locks manage the access to your door. Hence they should be treated as security devices – not just a gadget. You need to consider their mechanics, hardware, and digital aspects on the same level.
When looking for smart door locks, check if the producer supplies precise documentation of its security attests – standards set by external bodies. With lock cylinders, look for international security classes or ratings. There are strict European norms or ratings of door locks, set by local bodies, such as SKG-IKOB.
Make sure you purchase a smart lock from a trustworthy seller. For example, products sold outside of Europe are not required to be meet the EU norms, certified with the popular “CE” sign. Hence these are not tested for safety of use and compliance with applicable directives. Declaration of conformity should be publicly available on the smart lock’s producer website.
With digital security, which is not always certified by national authorities, you need to trust a specialized external organization with years-long experience in cybersecurity. One of the leading ones is AV-Test, which has approved several smart locks from the market. You can browse and read their reports here.
When choosing most smart door locks, the general advice would be to read about a smart device BUT NOT just on its producer’s website. Look for independent reviews written by independent bloggers, journalists or organizations. Producer of smart locks should always direct you to their documents or reports. If it wasn’t tested by independent specialists, you do not wish to test their security yourself.
Conclusion: can you trust smart locks?
Remember that no single solution can ensure complete, hackerproof security. That is why tedee uses a complete ecosystem of encryption, data storage, communication protocols, and permission management. It is extremely unlikely all of these fail or are broken into at once, isn’t it?
A high-quality smart lock combines convenience, the best lock hardware and the ultimate digital security standard. If you consider buying one, your manufacturer must be open and transparent about the technologies used in both parts of your home security. If any of these is not certified nor tested, you should not trust it, period.
Now that you know what makes smart door locks safe, look at how it works in practice. Protective solutions are used at every step of its operation. Now that you know more about them, and how convenient they are, you can decide if you trust it yourself and enjoy all smart locks benefits straightaway.
If you have any more doubts about matters not discussed here, we would be grateful to let us know at [email protected]. We will do our best to address your questions and update this article with more information to help other customers think about making their doors smart.
We believe and trust our products, and are determined to give you full and transparent information, so you can decide and enjoy it, too.
Reach the author of this article at [email protected]